If you watched last night's episode of Mr. Robot, you witnessed Elliot perform some hacking magic to decrypt Romero's keylogger files. The following is an explanation of what actually is happening in that scene, and what assumptions the writers of Mr. Robot are making.
The scene starts off with Agent DiPierro logging into an FBI computer from Agent Santiego's car. Next, she hands over access to Elliot who in a minute or two has completey decrypted Romero's keylogger files. A good place to start is by explaining what is a keylogger? A keylogger is just a hardware device or a software program that records the real time activity of a computer user including the keys they press. Romero had one running during the initial Evil Corp. hack, which could have the private keys to undo it.
The FBI had Romero's key logger files but he encrypted them with a password. Thing is .. the FBI didn't know Romero, I do.
When referring to a computer hard drive, a partition is a section of the hard drive that is separated from other segments. Partitions help enable users to divide a computer hard drive into different drives or different portions. The steps to encrypt one of these partitions is pretty simple. Romero would have most likely used the program cryptsetup to setup the cryptographic volume, and a quick overview of how this could have been is below.
- Copy data
The first step is to copy the data from somewhere on disk. The reason is because you can't change an existing partition into an encrypted one. First the data is copied somewhere, then you create the encrypted partition, and copy the data back to it.
- Format the partition with LUKS
LUKS is the standard for Linux hard disk encryption, and encrypts entire block devices and is therefore well-suited for protecting the contents of mobile devices such as removable storage media (usb pen) or laptop disk drives. It does not only facilitate compatibility among distributions, but also provides secure management of multiple user passwords. If you have a partition that is ready to use, you can prepare it with "cryptsetup luksFormat". You'll then be asked to set a password for use with the encryption. This was where Romero set the password that Elliot brute forces using song lyrics.
cryptsetup -y -v luksFormat /media/keyintercept_1WARNING!========This will overwrite data on /media/keyintercept_1 irrevocably.Are you sure? (Type uppercase yes): YESEnter LUKS passphrase:Verify passphrase:Command successful. - Format the partition
The partition is now available, but needs to be formatted with the normal filesystem tools to be usable. You can use a tool like mke2fs to create the new file system. Once the file system is created you can mount it, which just means placing access to the file system contained within onto your root file system structure. Effectively giving the files a location.
- Copy data to the partition
The data copied in the first step can now be placed on the partition, where it is fully encypted and password protected.
The next thing we see is Elliot running a python program from a shell. Python is a general purpose programming language, and a shell is just an interface to the operating systems services.
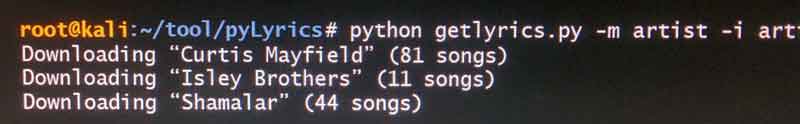
The command Elliot runs is pretty straighfoward. The important parts are that he has a script called "getlyrics.py" that he executes, and he passes in the name of a text file called "artists.txt" which most likely is a file with the names of artists Romero liked.
# python getlyrics.py -m artist -i artists.txt -o lyrics.txtWe can see that Elliot is running Kali linux, but it's unclear if the FBI machine he is using runs Kali, or if he's logged into a remote machine. Why is this important? In order to run the python program "getlyrics.py" the system Elliot is using needs Python installed, along with other packages like PyLyrics, (which downloads song lyrics) and the script he executes "getlyrics.py" would also need to be present on the machine filesystem (or accessible from somewhere).
The more likely scenario would be that Elliot SSH'd into a remote server that he controls, where he has everything he needs installed already. In order to login to said server Elliot would also need to have his private key (assuming he disabled password logins, which is highly likey for a super hacker like Elliot). Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network, and a private key can be thought of as a really long password. So long, that it's extremely difficult to brute force. It's also possible Elliot stored the scripts and files he needs on a public server somewhere (or thumb drive) and just downloaded them as needed.
The scene does not show that Elliot logged into a remote machine so we'll just assume he's running the commands on the FBI machine locally, and everything is installed and ready to go. After Elliot executes the script, we see that some songs are being downloaded. What exactly is happening here? We here Elliot mention that he "knows Romero". This is impying that Elliot knows how Romero might have picked a password for his encypted files. We can assume the code in the script Elliot runs is downloading song lyrics from artists Romero listened to. What might the code for something like this look like? It's actually pretty trivial.
# PyLyrics is a python module to get Lyrics of songs from lyrics.wikia.com
# It has support for getting albums of a singer and songs from an album from which lyrics can be accessed
from PyLyrics import *
# Read in the file that has a list of artists Romero liked
artists = open(sys.argv[4], 'r')
# This is the output file using the argument from the command line
# All the lyrics will be written to this file, and is later
# used as a list of passwords to test against the encypted file password
lyrics = open(sys.argv[6], 'w')
# For every artist, get a list of tracks and download the lyrics
for artist in artists:
albums = PyLyrics.getAlbums(singer=artist)
# Loop through every album and get the tracks
for album in albums:
tracks = album.tracks()
for track in tracks:
We download the lyrics and write the output to our lyrics file
lyrics.write(track.getLyrics())
artists.close()
lyrics.close()
After the code above is done executing, we're left with a file "lyrics.txt" which has a bunch of song lyrics in it. A portion of the output would look like something below.
Next we see Elliot brute force the LUKS encypted drive with a bunch of passwords. It appears that Elliot is using a program called bruteforce-luks. This program must be compiled and configured first. If Elliot is running directly from the FBI machine (and not a remote server) the program would have either been compiled before or he would have had to do that once he got access from DiPierro. Either way, we don't see this step and can just assume it's already been compiled and ready for use when Elliot starts using the machine.
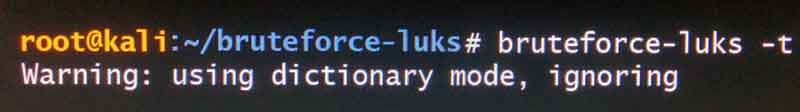
We see that Elliot is running "bruteforce-luks" in dictionary mode. This means the program tries to decrypt at least one of the key slots by trying all the passwords contained in a file. The file must have one password per line. We can see in the episode that the password found is "And if there's hell below We're all gonna go". What this tells us is that the program Elliot executes would also most likely need to do some processing to generate a full lyric on each line. We can also see from our lyrics output that the lyric containing the password has parenthises at the end inclusding some extra content (gonna go, gonna go, gonna go, go) . This is not part of the password so the program would also need to remove extra tokens like this, and also combine multiple lyrics per line.
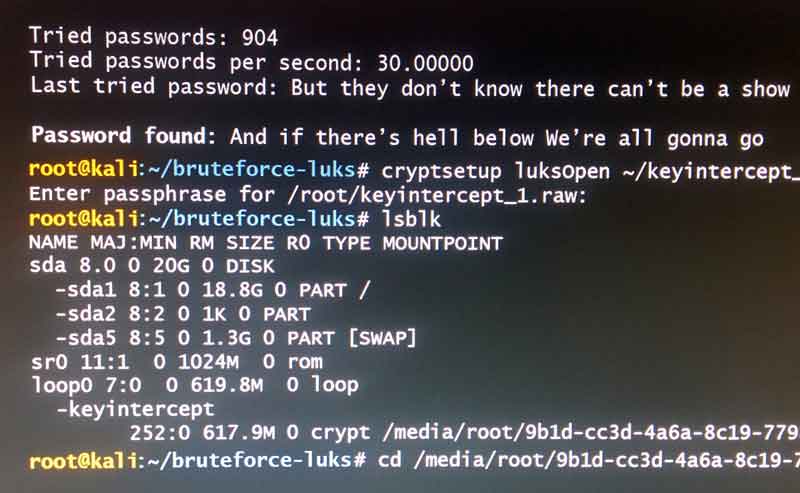
Brute forcing a password this way is definitley possible, but using song lyrics is pretty unreliable as you can see. Since the program to bruce force uses each line of our dictionary to test the LUKS volume, the lyric has to be exactly right. The output file with lyrics would have needed a line with the following lyrics exactly. That means no extra spaces, apostraphes, commas, brackets, missing letters, etc. If Romero had used "there is" instead of "there's" we would not find the password; if Romero used "going to go" instead of "gonna go" a password would not have been found. If the lyrics website (lyrics.wikia.com) had returned a lyric with an extra space somewhere, the password would not have been found. There are so many places this could fail that it almost isn't worth the effort, but when he fate of undoing 5/9 relies on it, it's definelty worth a shot!
Once Elliot gets the password, decrypting Romero's files becomes pretty trivial. All he does is use the same program from before (cryptsetep) and use the password found to decrypt it.
# cryptsetup luksOpen ~/keyintercept_1.raw keyintercept
The next step is to open the partition and set up a mapping name. It's here where Elliot will have to enter the passphrase to decrypt the partition. The mapped partition is now available in ~/keyintercept_1.raw/keyintercept but it isn’t mounted. The last step is create a mount point and to mount the mapped partition. Elliot can now open the files and view them directly in plain text. In the episode, it looks like Elliot had already mounted the drive, and uses lsblk to get information about it. lsblk lists information about all available or the specified block devices. The command prints all block devices in a tree-like format by default. It's this command that shows Elliot where the exact location of the data he wants is.
This is it, everything that was typed on those machines at the arcade on the night of the hack.
Using a program called bruteforce-luks, Elliot is able to use the lyrics file he generated to bruce force a password and decypt Romero's files. He performs these steps in what apears to be a minute on the show, but this would definitly take some time to setup at least. We don't see him generate the artists file, or write the code for retriving lyrics, or install any software. If all those things were done and setup perfectly for Elliot when starting, then a minute or two for the hack seams reasonable.
In conclusion, this is definitly a plausible hack, and it's fun to see how the writers come up with these scenarios. In reality, trying to find the password the way Elliot did would be pretty hit or miss, and it would take some time setting up the environment (installing programs, writing the code, etc.). The key piece of information to take away from this hack is that it all comes down to Elliot knowing that Romero used a song lyric in his password. He also needed to know which artists specifically, and that his password would be an exact match to a lyric from a song by that artist.